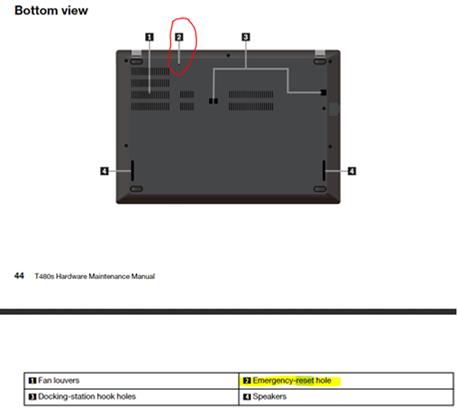
If you have a Lenovo laptop with a built-in battery and it won't power on or wake-up from a sleep state, you can use the pin-hole emergency reset hole (button) to resolve the issue.
Disconnect the power adapter and depress this button with a paper-clip or similar item. Wait for 1 minute, then reconnect the AC adapter or power up using the battery.
The location of the reset button varies by model. The location for a T480s is shown below (taken from the Hardware Maintenance Manual). You do not lose any settings or data. Best I can tell, this is the similar to removing a removable battery on older models.