For most customer networks, file servers turn into a mess over the years. This is usually due to a few things. First, users have access to make folders at high levels and then place data in those folders that should have access restricted. Second, users try to solve the first problem by securing those folders, but end up breaking access to administrator accounts. Third, most lack a logical structure or any guidance as to where certain documents should be stored, so documents end up in multiple folders.
I have been working with a customer who had all of these issues, along with the need to merge two file structures into a single structure after the merger of their two companies. My suggestion to the customer was to come up with a structure for five to ten top level folders that would be the shared folders. Their primary focus for the top level folders was by department (HR, Finance, Legal, etc.) We then tightly controlled the second to fifth levels, depending on the granularity needed of the specific folder. At the controlled levels, we did not allow users to make new folders or files and also prevented them from changing the permissions for these folders. We used a combination of list, read, and read/write access to all of these folders. We created an Active Directory group for each folder and the level(s) of access necessary for that folder. We then created additional groups in Active Directory based on job role and made these groups members of the Active Directory groups used for setting permissions on each folder.
After setting all of the folder permissions, I found that the Owner of the file or folder had Full Control even if they should not have this level of control based on the NTFS permissions. This can be fixed by setting OWNER RIGHTS to none, which will cause the permissions explicitly defined to be enforce and not be circumvented by OWNER RIGHTS.
The partial folder tree shown in the screenshots below is as follows:
- Shares – OWNER RIGHTS permissions set
- (Other folders not shown)
- Internal Reports – List permissions
- Containment – Read only and Modify permissions set
- Internal Reports – List permissions
- (Other folders not shown)
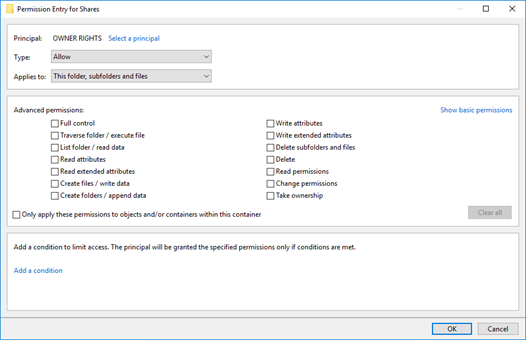
Example of OWNER RIGHTS permissions. Notice no boxes are selected, which causes the owner to have no rights and the other defined permissions to be used:
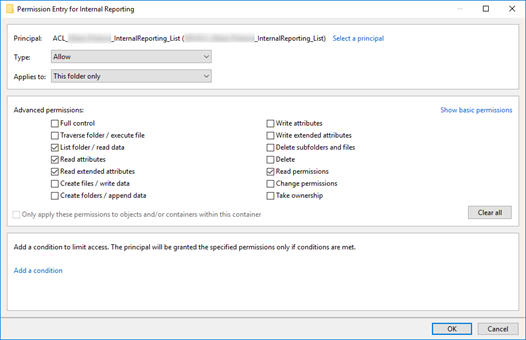
Example of the Internal Reporting folder with list permissions:
Example of the Internal Reporting\Completions folder with read only access:

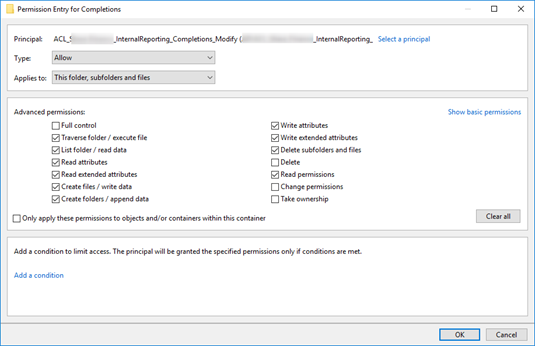
Example of the Internal Reporting\Completions folder with modify access. Notice "Delete" is not selected, but "Delete Subfolder and files is". Delete is the value in the "Modify" permission set, so this change makes this not truly "Modify", but rather "Special":