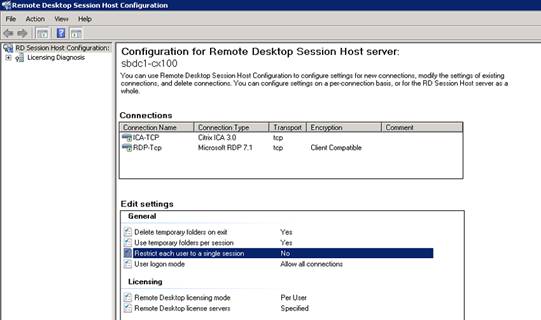
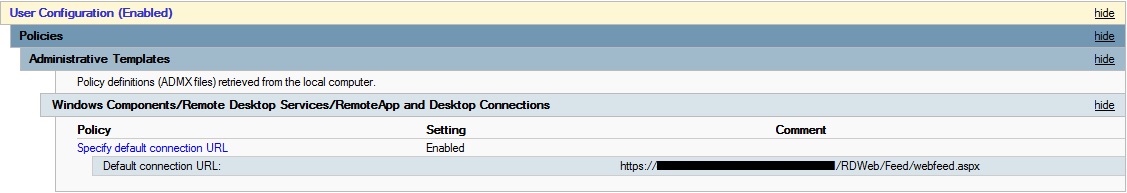
The Microsoft Assessment Planning (MAP) Toolkit is a useful utility that can be used to gather hardware and software information for workstations and servers. After installing the toolkit, you can provide domain credentials which it uses to poll each device in Active Directory and gather information about the devices it finds. This data can be viewed through various Excel reports and can help to shorten the time it takes to fill out an audit questionnaire.
The toolkit can be downloaded from: https://www.microsoft.com/en-us/download/details.aspx?&id=7826

- Products
- Services
- About
- Resources