If you experience a hardware failure with a VMware host, run the following commands to create a plain-text diagnostic file which will help you determine where the failure exists: [more]
- Connect to the host via SSH
- Log in as “root”
- Type: “cd /opt/hp” and press ENTER
- Type: “ls” to list the contents of this directory. Verify hpacucli is listed
- Type “cd hpacucli/bin” and press ENTER
- Type “./hpacucli” and press ENTER
- Type “controller all diag file=/tmp/adu.zip” and press ENTER
- Once the diagnostic report has been generated, use WinSCP (or a similar application) to connect to the host
- Browse to the tmp directory
- Copy the adu.zip folder locally
- Extract the files and open the “ADUReport.txt” file to view the results
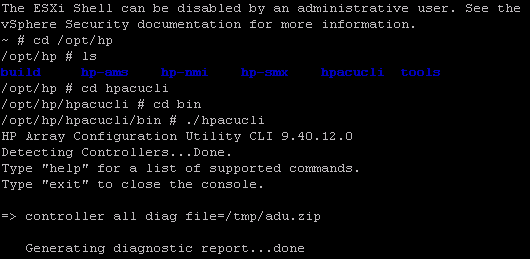
The diagnostic result file can be large, so you may have to do some searching before you find where the failures exist. Also this documentation is specific to HP products so commands/file paths may for different hardware manufacturers.