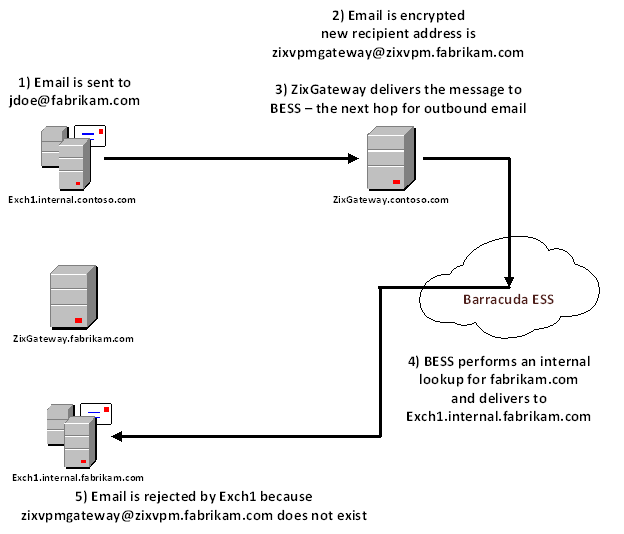
I’ve been migrating Exchange customers from Barracuda ESS over the past few months and recently ran into a small issue. I had logged into the BESS portal one morning and decided to go ahead and start cleaning up some of the domains that were registered so that Barracuda would stop routing email for these customers.
It was a simple enough process – Click the Domains tab, find the domain to remove, click Remove. Everything magically disappears.
I removed 23 domains and called it good for the morning and proceeded to work on other things. A few days later, we get a task from a customer who was unable to receive email from another customer of ours who was still using Barracuda ESS. After tracking down the logs in Customer #2’s BESS portal, I discovered that BESS was still routing email internally instead of respecting MX records.
A quick phone call to Barracuda Support and they immediately escalated the case to Tier 2/3 and Product Development. I heard back from them later that afternoon and was informed that I was removing the domains incorrectly.
I didn’t think I could screw up clicking a “Remove” button, but apparently I did.
After another minute or two of explanation, my support rep explained that the issue was really because the domains I had removed that included Aliases. There’s apparently an acknowledged bug with the portal that requires you to un-alias all domains before removing the parent domain from the portal. They checked all 23 domains I sent and verified we were good to go.