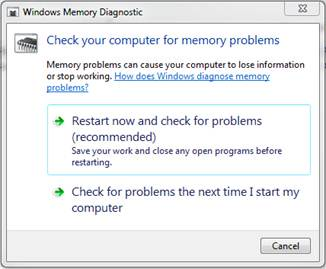
Typically, we run memory diagnostics from a bootable CD, but if you are trying to troubleshoot a computer in another city this is not always possible. Windows 7, Vista, Server 2008, and Server 2008 R2 have a built in utility called mdsched.exe. The utility can be started from a Windows session and will start automatically at the next reboot. The default is a simple memory diagnostic, but extended testing can be performed. Results will display during the test, on screen after the test, and in the Event Viewer under Applications and Services > Microsoft > Windows > MemoryDiagnostics-Results > Memory Diagnostic Tool after the test is complete.
More detailed information can be found here: [more]
http://www.sevenforums.com/tutorials/715-memory-diagnostics-tool.html