When working on a compromised system, it's always good to have a "toolkit" available on read-only media (in case built-in utilities, like netstat, have been replaced on the compromised machine to hide the attackers activities). However, you also need to know how to USE the tools in your toolkit. At my training last week I was working to recover a compromised web server. After doing some cleanup and removing some clearly malicious software, I tried to use netstat to verify the current listening ports/services on the machine (along with associated processes). The local netstat on the machine had been hacked to return no output, but thankfully the netstat EXE on my "toolkit" CD was working. I quickly combed through the list of ports that were labeled "LISTENING". I didn't see anything listening that was out of the ordinary. However, when the following prompt popped up I knew the attacker still had remote access to my machine. [more]
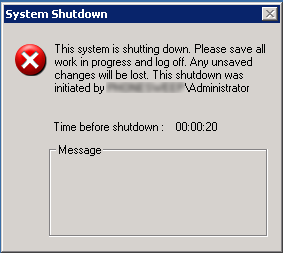
Upon a closer look at the netstat output, I noticed there was an "ESTABLISHED" connection to TCP port 23 on my host (typically used for telnet). P0wn3d!
Lesson learned… verify ESTABLISHED sessions in addition to actively LISTENING services.
