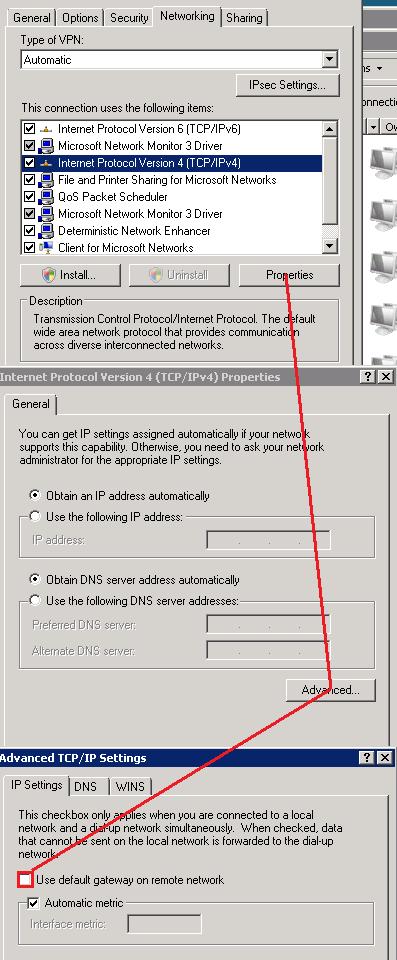
I came across a problem in one of our automated Robocopy command scripts when copying files from NTFS to EMC Celerra file system. The problem was that every time Robocopy was told to copy files to the EMC Celerra over the VPN, the files were always detected as “newer” on from the originating source. This caused Robocopy to copy every single file from our network to the remote network each and every time.
I came across a command line switch for Robocopy: /FFT : Assume FAT File Times (2-second date/time granularity). So what this does is force Robocopy to use FAT style time stamps which are 2-second granularity. It allows enough flexibility to account for the way the time is recorded when doing a file copy from NTFS to another file system. This is needed when going between and NTFS and Linux/Unix/FAT or emulated file system.