Windows 2008 and IIS 7.0 installs with Secure Sockets Layer (SSL) version 2 and “weak” cryptography ciphers turned on by default. Having that turned on will likely turn up some problems in a penetration test. Here are some common vulnerabilities names that might be identified in your penetration test results:
-
SSL Server Supports Weak Encryption
-
SSL Server Allows Cleartext Encryption
-
SSL Server May Be Forced to Use Weak Encryption
-
SSL Server Allows Anonymous Authentication [more]
Disabling
Unfortunately, there is not currently an intuitive way to enable/disable the protocols and ciphers built into the Windows GUI. You must edit your systems registry to get the job done. Some of the registry keys and DWORDs will likely not be in the registry, so you will need to add them. It’s always a good idea to back up your registry before making changes just in case something goes wrong. Click Start, click Run, Type regedit32 or type regedit, click OK, and then add/modify the keys listed below.
Here are the registry keys to turn off PCT 1.0 and SSL 2.0 and leave SSL 3.0 and TLS 1.0 turned on:
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server
-
DWORD = 1
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server
-
DWORD = 1
-
Here are the keys to turn off “weak” SSL ciphers:
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\NULL
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 56/128
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128
-
DWORD = 0
-
-
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128
-
DWORD = 0
-
Testing
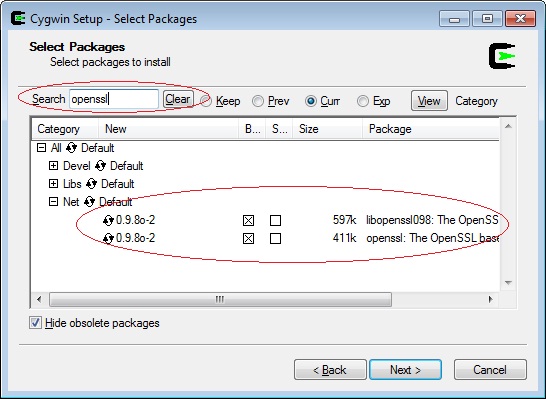
The easiest way I’ve found to verify the protocols and ciphers are turned off is to use the free OpenSSL toolkit. Here are some instructions for installing Cygwin with OpenSSL on Windows 7: https://www.conetrix.com/Blog/post/How-to-Install-OpenSSL-on-Windows-7.aspx. Here are some instructions for installing OpenSSL on Ubuntu: https://help.ubuntu.com/community/OpenSSL#Practical OpenSSL Usage. If you are using a Mac OpenSSL should already be installed. Once you get it installed you can verify your registry changes worked.
Once you get it installed here is the commands you can use to verify that SSLv2 is turned off:
# openssl s_client –ssl2 –connect YOURSERVERNAME:443
If server does not support SSLv2 then you should see an error like the following two examples:
CONNECTED<00000003>
Write:errno=113Or
CONNECTED<00000003>
1324:error:1407F0E5:SSL routines:SSL2_WRITE:ssl handshake failure:s2_pkt.c:428:
Here is the command to test for weak ciphers:
# openssl s_client -connect SERVERNAME:443 -cipher LOW:EXP
If the server does not support weak ciphers then an error will be displayed similar to the error examples given above.