One of our customers is running Symantec Mail Security for Microsoft Exchange 5.0. We were having trouble with the service hanging up in a "Starting" state when the server started up. [more]See below the picture below.
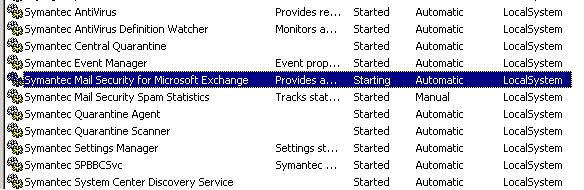
I wanted to delay this service from starting up until the server boot process was further along. Using the command “sc query”, I was able to see the Service Name: SMSMSE that matched up with the Display name in the services list.
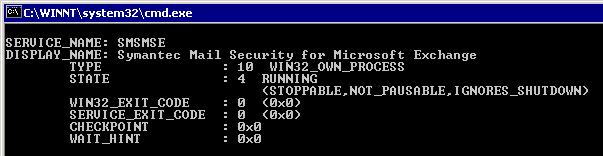
Since the service was hung up, I could not set the service startup type to disabled or manual. In the service properties, Log On tab, click the disable button to disable the service from starting up for the hardware profile, and reboot the server. After the server has rebooted, make sure to go back and “Enable” the hardware profile.
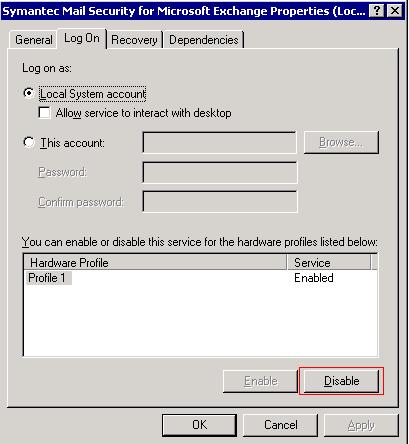
While the server was booting up, I connected to the services list of the server from another PC. This way, I could see which services were starting up towards the end of booting. One of the last services to start was “Microsoft Exchange Information Store”. Knowing that, I needed to find the Service Name to match the Display Name. Using “sc query” again, I found the service name to be MSExchangeIS.
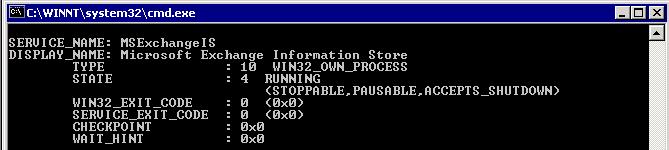
In order to get the SMSMSE service to startup AFTER the MSExchangeIS service started, you have to specify that SMSMSE depends on MSExchangeIS to be started before it can start. To do this, open regedt32. Regedit will not work in this case because we have to edit a REG_MULTI_SZ key. Go to the following location in the registry: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\<Service name>. The key to edit or add is “DependOnService”. In this case, I added “MSExchangeIS” to this list so the service would not try to start until this service was started.
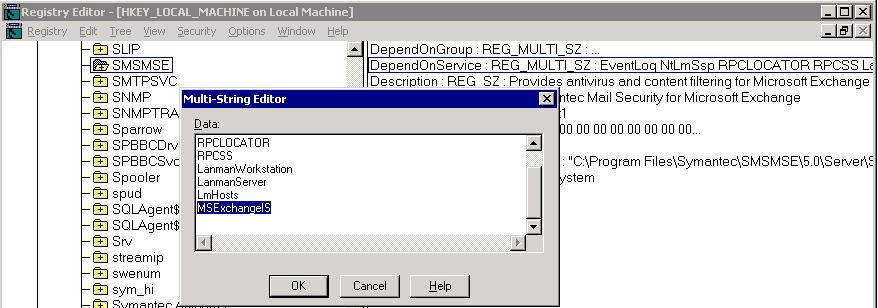
After this change was made, the SMSMSE service was delayed long enough for it to be able to startup automatically.
