A client's users were getting an error that prevented them from logging into their terminal server. The error points to a long file path for a certain file that is too long to be copied during their roaming profile transfer. After some research we found that Internet Explorer creates drive cached XML files that are stored within the user’s profile. The file path is so extensive that it prevents windows from copying the file during the roaming profile transfer.
In this particular case, the files are stored in two different places. [more]
-
The USERDATA folder in the root of the profile path.
-
Application Data\Microsoft\Internet Explorer\UserData
We are able to fix the issue with Location #1 by using a Group Policy to restrict what folders are copied back and forth during the roaming profile. By adding the USERDATA folder to this policy, these files are no longer copied with the roaming profile.
Location #2 is still being researched. However, it appears this caching location can be disabled as well within the internet option settings. It hasn’t been tested at this point, but could be a possible solution.
The setting is located in the following location:
1. Within Internet Options, select the Security Tab, then the Internet Zone, then Custom Level.
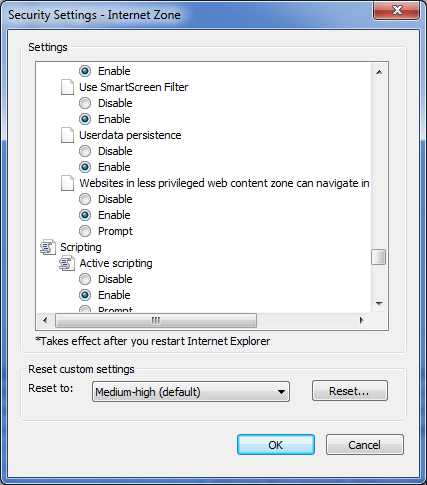
2. Within the Security Settings, Disable Userdata persisitence

