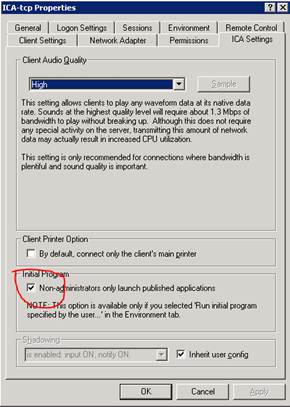
One of our network consulting clients complained of being unable to use remote logon for shadowing sessions on a terminal server. Upon testing I was able to use remote logon fine. I did eventually find a user that I could not shadow. I received an error, “Access is Denied” when attempting to use remote logon with their session. Further investigation found that users that had two monitors setup and were using both with remote desktop 7 were the ones I could not remote to. This had been confusing because sometimes it appeared to work and others it did not. The customer was in the process of moving all users to a two monitor setup so the problem had been progressively getting worse. Various forums and Microsoft articles referenced this problem. Shadowing of dual monitor sessions is not currently supported by Remote Desktop Services Manager.

- Products
- Services
- About
- Resources