I came across a problem with OWA where it kept redirecting the external server address to the internal server address (Ex. Mail.public.com -> servername.domain.dom).
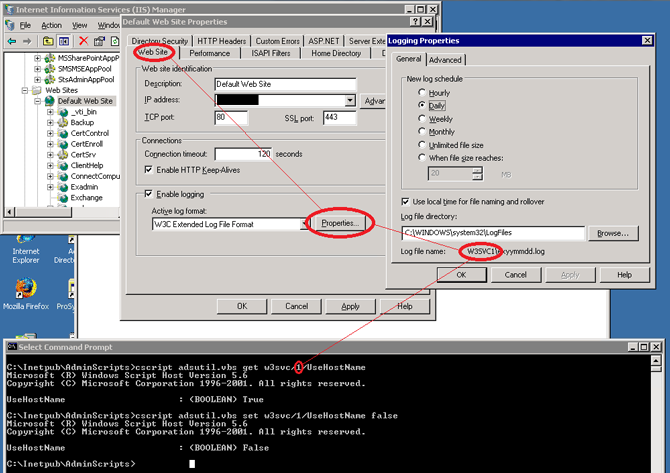
After doing some thorough research, I discovered that there is a property in the IIS Metabase file that controls whether or not the server name is always used. Microsoft KB article 834141 says that “The UseHostName property will instruct IIS to always replace the SERVER_NAME variable with the fully qualified machine name.” This property is a Boolean value. Setting this property to false stopped the automatic redirects and kept the external server name in the web browser. [more]
In order to edit the metabase, you must use commands with adsutil.vbs. You must have the site ID of the website you want to edit the value for. I show in the screen shot below how you can view the log file name in order to determine the site ID number. I then show the commands used to get and set the UseHostName property for the website.