There has been a lot of discussion about whether a BitLocker pre-boot PIN increases security or not. The primary argument we have had is related to the PIN providing a layer of security between an attacker with physical access and the Windows credentials.
If a user is running Windows 8 or later and has encrypted the OS volume, there is a GPO designed to protect against Windows password guessing. If Windows credentials are cached, which is common for laptops, it is possible to bypass account lockout settings if the system doesn't have access to a domain controller. However, this GPO will help protect a system even if it can't reach a domain controller.
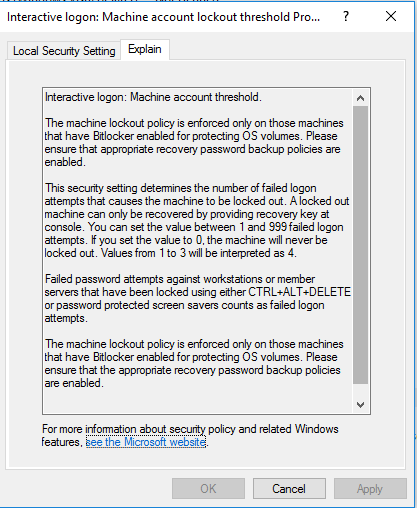
Administrators can set the “Interactive logon: Machine account lockout threshold” Group Policy under \Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options.
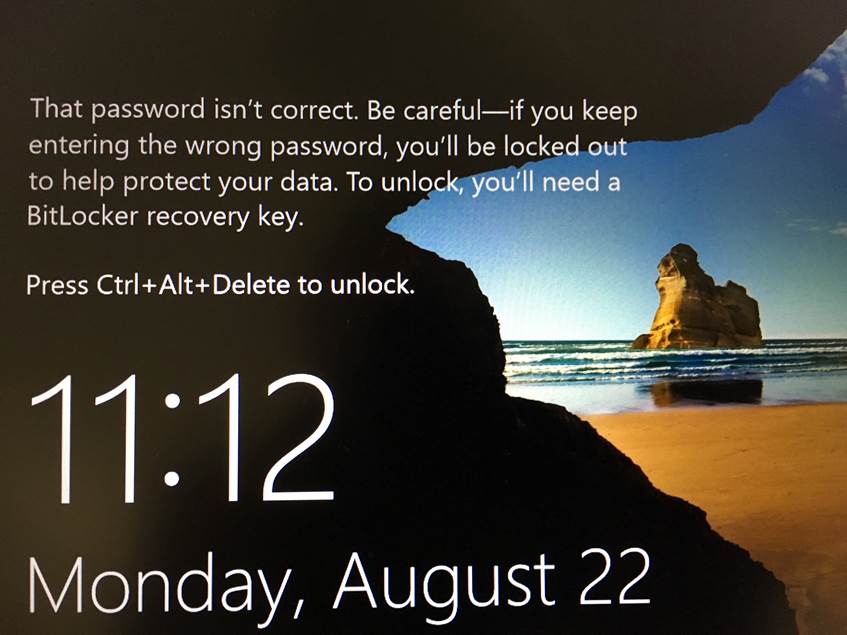
When applied, this setting will cause the following message to be displayed shortly before the machine account threshold is reached. After the threshold is exceeded, the system will reboot and require a BitLocker recovery key in order to boot.