When you enable SSLVPN or HTTP/HTTPS for Management on your WAN interface on a Fortigate, the Fortigate creates global system Local-In policies. These are built-in policies that allow all traffic to the ports and services for SSLVPN and management on the WAN interface by default.
When you put in a Geoblocking rule to block traffic to or from certain countries on your Fortigate under IPv4 Policies, that will not affect these system Local-In policies, even if you put in an IPv4 policy to block all inbound traffic from certain countries. There are a couple of ways to fix this.
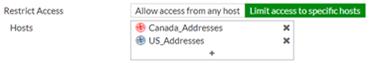
The first option is the most restrictive and would probably be the best. This option is to specify only the addresses you want to have access to these services when setting them up, which will prevent a global system Local-In policy from being created. When setting up SSLVPN, instead of allowing access to all hosts, you can specify only the IPs or countries you want to have access to the SSLVPN ports from the outside. (You need to have already setup the address objects for the IPs or countries you want to have access).
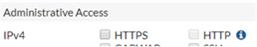
To restrict management from the outside, under the WAN interface, simply don't enable HTTP or HTTPS. That will prevent the default Local-In policy from being created.
If you do need external management access, you'll then need to create a custom Local-In policy to allow access on those ports from the network from which you'd like to access it. We typically add the entire company external subnet. Just be sure that this network is also added as a trusted host under your system administrator's account (System -> Administrators)
Custom Local-In polices can only be created via CLI. The following CLI commands will create this custom Local-In policy. These commands assume that you've already created address objects for your WAN IP named Wan1_IP and the public subnet named "External", a service object for your web management port named MGMT, and assume that your WAN interface is wan1.
config firewall local-in-policy
edit 1
set intf "wan1"
set srcaddr "External"
set dstaddr "Wan1_IP"
set action accept
set service "MGMT"
set schedule "always"
next
end
The second option is to just leave those default system Local-In policies in place, but then to create custom Local-In polices to block access to SSLVPN and management services from IP addresses or countries that you don't want to have access
Again, since this is a cusom Local-In policy it has to be added via CLI. The following CLI commands also assume that the address and service objects have already been created for your WAN IP, for the countries you want to block, for your SSLVPN and management services, and that the WAN interface is wan1.
config firewall local-in-policy
edit 1
set intf "wan1"
set srcaddr "Blocked Countries"
set dstaddr "Wan1_IP"
set action deny
set service "SSLVPN"
set schedule "always"
next
edit 2
set intf "wan1"
set srcaddr "Blocked Countries"
set dstaddr "Wan1_IP"
set action deny
set service "MGMT"
set schedule "always"
next
end
