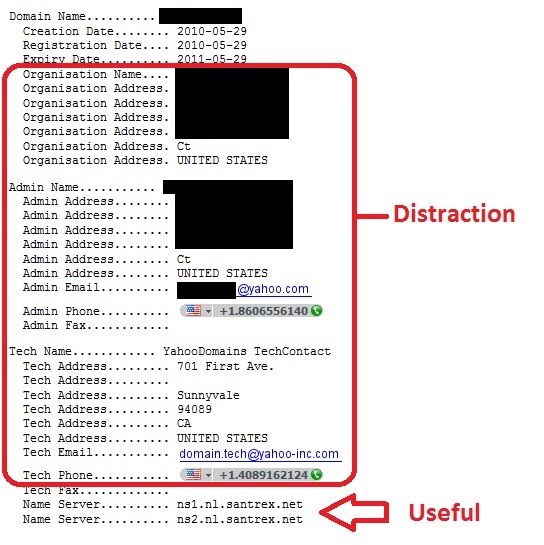
Steve Gibson, one of the hosts of the popular "SecurityNow!" podcast, has created a tool that allows the checking of DNS servers for spoofability. This tool works by asking the user's browser to retrieve an image located at a uniquely named subdomain of the type xxxxxxxxxxxxx.dns.grc.com, "where the “xxxxxxxxxxxxx” is replaced with a unique 13-character string of characters that has never been used before."*
Then, in order to know the IP address for this special domain, the browser sends a DNS query to its DNS server, which then forwards this query to a special nameserver located at grc.com. This nameserver tells the DNS server that the location of that image is actually an "'alias' of the real domain name, which is a good deal longer and more complex."* The nameserver instructs the DNS server to look up the name of the "real" location of the image which looks like "...a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.a.xxxxxxxxxxxxx.dns.grc.com"* (with about 50 preceding 'a''s) [more]
The DNS server sends queries to the GRC nameserver, attempting to resolve the IP address of the given domain name one sub-domain at a time , causing the DNS server to send hundreds of requests which are collected by the GRC nameserver. As the nameserver collects these requests, it creates a scatter plot of both the Source Port and the Query Transaction ID of each request. Then, the data is analyzed to see the randomness of the Source Port and the Query Transaction ID which reveals the spoofability of the used DNS servers.
This tool is quite interesting, and shows that even as vulnerabilities arise on these critical systems, many do not fix the vulnerabilities, leaving the users at risk to visit a malicious web site believing that it is the site they were looking for which potentially places their private data at risk.
*A more thorough and detailed analysis of how this tool works can be found by reading GRC's article on how the DNS Nameserver Spoffability Test works.