If you are like most leaders in an organization, you don't have the time or motivation to do any sort of cybersecurity assessment to mitigate risk. It's easy to question security testing and ask, "why bother." After all, doesn't it take a lot of effort to do security testing when it may not turn up any results?
However, much like a regular visit to the doctor's office for our physical health, you should find ways to regularly "check up" on your organization's cybersecurity posture. Much like a check-up with a doctor, finding irregularities or vulnerabilities early allows you to implement mitigating controls before they cause harm.
How do you manage your cyber risk? What vulnerabilities are you facing? How can you know?
In this article, we are going to discuss five "check-ups" you can do now to secure your future.
Internet Vulnerability and Exposure Assessment (IEVA)
Let's start with the external evaluation, and is similar to a doctor when he asks questions and pokes around. This is an external evaluation. It is not really an invasive procedure, and by no means will it catch everything, but it does allow the doctor to look for warning signs and make an informed decision about next steps.
The same kind of external evaluation should be performed for your network. We like to call this an "Internet Exposure and Vulnerability Assessment" or IEVA, for short. An IEVA can identify how a potential attacker can target your system from outside your network. It is designed to review controls protecting your external presence, including your perimeter devices, servers, applications, and encryption technology.
Evaluating the external perimeter of your network allows you to identify vulnerabilities in your first lines of defense. This level of knowledge allows you to focus your resources, both monetary and time, to areas providing the biggest impact making your security more efficient and effective.
An IEVA is a great place to start, but remember, this is a high-level observation. For a full assessment of external vulnerabilities, there is always one step further you can go, which is a full-on network penetration test. You can think of this as a referral from your primary care physician to a specialist. They may perform some of the same tests, but the goal is to discover and remedy flaws, which means more thorough tests may be performed.
When it comes to assessing the status of your external perimeter, consider the following questions.
- Have you had an external vulnerability assessment or penetration test performed on your network?
- What is the frequency of these assessments, is that frequency sufficient to ensure your external perimeter remains secured?
A strong external perimeter will dissuade an attacker as well as alert you to persistent attempts, allowing you to be proactive instead of reactive.
Internal Vulnerability Assessments (IVA)
Let's continue with the doctor analogy. When a doctor finishes his high-level assessment, he sends you over to have lab work done. These tests are a bit more invasive and look at things that could be wrong or right internally. With results from the lab, the doctor can make a more precise diagnosis about the status of your health, seeing if previous recommendations were working as intended, or if changes needed to be made.
An "Internal Vulnerability Assessment," or IVA, works in similar ways. An IVA is a credential scan, preferably with domain admin privileges. This scan can identify vulnerabilities that exist inside your network. An IVA can find vulnerabilities such as outdated software, missing patches, weak or outdated protocols, weaknesses in system hardening procedures, and many other known vulnerabilities.
With this information the Information Security Officer can make recommendations for additional controls that target these specific vulnerabilities, increasing the efficiency and effectiveness of your information technology infrastructure.
When assessing the status of your internal network, consider the following questions.
- What types of internal assessments have you performed on your network?
- How frequently do you conduct those assessments?
- Do these assessments test all your internal controls?
- Are the controls working as intended?
- Are they mitigating the known threats as designed?
- What proof are you relying on to verify the controls are working as intended?
- If not, what are your short-term and long-term plans for addressing those weaknesses?
Knowing your vulnerabilities and addressing them is an ongoing process. Threat landscapes are constantly changing as are the vulnerabilities facing your organization. Constant evaluation and upkeep are required to maintain a secure environment.
Security Awareness Training
Another way a doctor might help you physically is to provide some literature on natural ways to improve health. As you may know, people adapt to the culture that surrounds them when it comes to healthy living. If those around you eat healthily and exercise, then you are likely to do so as well.
Culture sets the tone for nearly everything we do in life and security awareness is no different.
When assessing the status of your organization's security awareness culture, consider the following questions.
- Is maintaining a high level of information security part of your culture, or is it a compliance box to check?
- Does your security awareness training focus solely on policies, or does it apply to your employees' personal and professional lives?
- Do your policies reflect security or convenience?
- Is information security addressed both formally and informally throughout the year?
- In your governance structure, who is accountable for the level of training provided (e.g., IT Director, ISO, CEO, etc.)?
For security awareness training to be impactful, it needs to happen frequently, be relevant to its audience, current in its content, and start at the top of the organization.
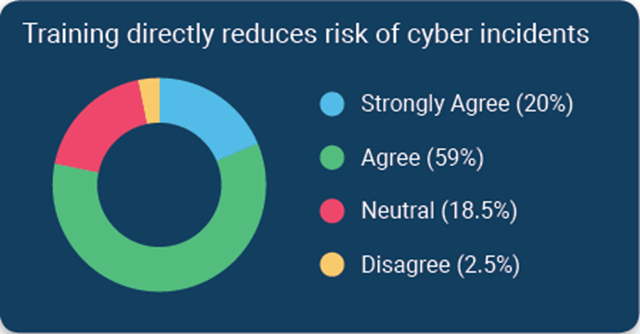 According to a survey of financial institutions conducted by Tandem, a CoNetrix Security partner, 79% of respondents stated they believe cybersecurity awareness training directly reduces the risk of security incidents. Download the 2020 State of Cybersecurity Report for additional trends and insights.
According to a survey of financial institutions conducted by Tandem, a CoNetrix Security partner, 79% of respondents stated they believe cybersecurity awareness training directly reduces the risk of security incidents. Download the 2020 State of Cybersecurity Report for additional trends and insights.
Simulated Phishing Tests
When we visit the doctor, he asks if you exercise, how frequently, and for what duration. The more you exercise, the better you feel. The better you feel, the more exercise you are willing to do.
Simulated phishing tests are similar to exercise. At first, your employees will think you are out to get them, but the more times they pass the test, the more times they recognize the phishing attempt, the more confidence they will have going forward, knowing they have the ability to thwart the bad guys.
An unfortunate, yet simple truth is the human asset is any organization's weakest point when it comes to information security. This is why phishing (or variants thereof) remains the most carried out cyber-attack. A particularly scary problem with phishing is that every time you put a control in place, attackers find a way around it. For instance, phishing used to primarily be about delivering a malicious file, getting the recipient to install the file, and granting the bad guy access. Today, this is still an employed tactic, but it is just as likely the attacker is trying to get the recipient to divulge important information.
Phishing tests should be frequent in nature and the results should be used to drive security awareness training. In the areas where you see success, highlight those in your next training. In the areas where you see weakness, follow up with an increased focus on identifying key elements of the phishing attempt.
Send out multiple types of phishing emails, requesting unique recipient interaction (e.g., download a file, ask for credentials or other confidential information, request immediate action, etc.). Maybe try vishing (phone calls) or smishing (SMS messages). Let your employees know that the principles for each type of social engineering are the same, and the outcomes are equally devastating.
While clicking a link or providing information is a failure, equally important is what the employee does once they have succumbed to the attack. How quickly did they notify the appropriate personnel? Was it quick enough to minimize the damage that could have been caused if the phishing email was real? Is this part of your security awareness training?
When assessing the status of your organization's simulated phishing training, consider the following questions.
- How often do you send phishing tests to your employees?
- What are you doing with the results?
- Are you diversifying the types of phishing tests carried out?
- What do you deem a "failure?"
- What type of follow-up training do you provide?
Phishing is so prevalent because it works, and it only takes one person to make that vital mistake. Awareness is the most important control you can put in place when mitigating this threat.
Strategic Planning
When you visit a doctor's office, it is common to discuss your family's medical history. You will look at issues that you could potentially face in the future, and determined a needed strategic plan to help secure your future. The plan will often include recommendations based on your current health and often includes a recommendation to consult with a specialist as a preventative or early detection measure.
Identifying threats allows you to put controls in place to mitigate what you know. Having a strategic plan in place allows you to prevent or respond quickly to the unknown.
Everything we've talked about up this point can help you identify where you are, but what is your plan to address the identified issues? How do you transition from identification to detection and prevention? How can you develop a sustainable plan? There are some basic elements, essential to any information security program that all organizations should factor into their strategic plan.
- A Business Continuity Plan, based on an impact analysis for each business unit to promote resilience and create restoration plans, in the event of a business disruption.
- An Information Security Risk Assessment to identify the threats your organization faces and the controls in place to mitigate the risk of those threats.
- An Incident Response Plan to document how your organization is going to handle an information security incident when it happens.
- Information Security Policies to define the overarching principals your organization will follow when it comes to users, system hardening, and use of organizational or personal assets.
When assessing the status of your organization's strategic plan, consider the following questions.
- What is the status of the organization's information security program?
- When is the last time the program was tested?
- What types of training and/or testing are you performing?
- Is the information security program part of your organization's strategic plan?
- If not, does your organization have the expertise or knowledge to change that?
If you are not sure about the status of your organization's information security program, or if necessary expertise does not exist, it may be time to look at a consultant to help put a plan in place for moving forward.
Securing Your Future
Sometimes, we all need a helping hand. When it comes to something as important as your health or the security of your network, an independent evaluation can help offer the tools you need to secure your future. If you work in a regulated industry, I look forward to hearing how your next audit, examination, and/or consultation goes, and the improvements you decide to make as we all mature together.
For your next steps towards securing your future, learn more about how CoNetrix Security can help at https://conetrix.com/security.
