 Not long ago, the Federal Financial Institutions Examination Council (FFIEC) announced and began its examination pilot program about cybersecurity activities, reviewing over 500 community financial institutions as part of its summer examination cycle. The FFIEC says the purpose of this pilot program is to "assess how community financial institutions manage cybersecurity and their preparedness to mitigate increasing cyber risks."
Not long ago, the Federal Financial Institutions Examination Council (FFIEC) announced and began its examination pilot program about cybersecurity activities, reviewing over 500 community financial institutions as part of its summer examination cycle. The FFIEC says the purpose of this pilot program is to "assess how community financial institutions manage cybersecurity and their preparedness to mitigate increasing cyber risks."
So, why the need for more guidance? Shouldn't our information security program address cyber-attacks? Well, it could, but do you know of many institutions that are fully prepared to address a cybersecurity incident, regardless of what the incident may be? Probably not. Regardless of desire for security, we are typically two steps behind attackers because they are the inventors of attacks. The new focus on cybersecurity is greatly directed toward improving the financial institution culture regarding cybersecurity, making it into a culture of corporate awareness and expectancy. You may notice that the FFIEC has emphasized a top-down structure, starting with the education of CEOs, through their informational webinar back in May. CEOs were encouraged to be bigger players in the cybersecurity sphere, due to the fact that every employee should be sensitive to the realities of cybersecurity. Admittance is the first step to recovery.
With the increased customer demand for new technologies, cybersecurity threats are exponentially increasing in number and in sophistication. Attackers now include nation-states, hacktivists, organizational criminals, and even malicious insiders. The motivations behind these attacks are even more diverse. It's not just about the money; it's about the message. And the one message that is present, regardless of the attacker's intention, is that customers cannot have confidence in the financial system. The loss involved is larger than money and larger than your institution. It is an attack on the sustainability of the system.
But enough scare tactics…
You can do something about this. Yes, you, the small (or medium) sized community institution. In some ways, you're more capable of protecting yourself than larger institutions are because you're dealing with less complex systems, thus you have fewer points of vulnerability. As of yet, there is no official FFIEC guidance regarding how your financial institution should manage its cybersecurity risk, but the current NIST framework has been pointed to as a likely candidate for an adopted cybersecurity framework.
If you're unfamiliar with the NIST "Framework for Improving Critical Infrastructure Cybersecurity," here's a brief breakdown. There are three key phrases you should be familiar with: Framework Core, Framework Implementation Tiers, and Framework Profile.
- The Framework Core is a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors, consisting of five concurrent and continuous functions: Identify, Protect, Detect, Respond, and Recover. This is a strategic view of the lifecycle of an organization's management of cybersecurity risk. Each function is broken down into categories and subcategories to be assessed.
- The Framework Implementation Tiers provide context for how an organization views cybersecurity risk and the processes in place to manage that risk. The four tiers, from 1 to 4, are: Partial, Risk Informed, Repeatable, and Adaptive.
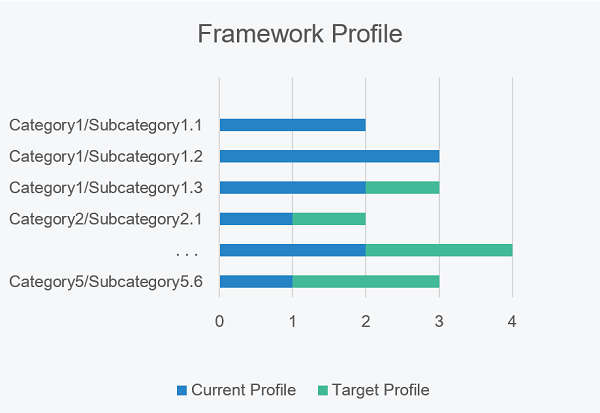
- The Framework Profile is a self-assessment displaying the difference in alignment of the institution's current core-tier levels with the target core-tier levels. The target profile is based on the business requirements, risk tolerance, and resources of the organization.
No matter which framework is adopted, the first step to a strong cybersecurity program is the acknowledgement of cyber-threats and the impact they can have on the bank, immediately followed by bank-wide education of cyber-threat red flags and the coinciding appropriate responses. A few additional items may be asked of you as well, including your financial institution's cybersecurity policies, risk assessment, responsible parties, testing program and results, monitoring, incident response and reports, internal controls and vendor controls, all electronic connections, and threat intelligence resources. You shouldn't have to completely build a cybersecurity program from the ground up. A lot of this information you already have, but perhaps it's branded as "Information Security." This is not a new concept, just a renewed attention to the most swiftly evolving threats facing financial institutions today.

