A few weeks ago, I was trying to backup the configuration for a Symantec Mail Security Appliance for one of our clients. The appliance sits in the DMZ and FTPs the backup file to another server on the internal network. To do so, I had to create an Access Rule to allow the FTP traffic through the ISA 2004 server. You would think that creating an inbound Access Rule to allow the FTP protocol to pass through the ISA server it would enable all inbound FTP traffic. However, this is not entirely the case. When you use the New Access Rule Wizard, you can choose the pre-configured protocol “FTP” to be the type of traffic that you are allowing. This is what I did in this particular instance. However, whenever I would try and transfer the SMS Gateway backup file, the write would fail. After checking folder and FTP account permissions 5,000 times, I happened upon a setting the following setting by right clicking the the access rule I had already created and selecting the "Configure FTP" option: [more]
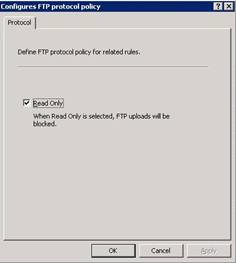
To make a long story short, when I added the preconfigured “FTP” protocol as the protocol I wanted to allow to pass through the ISA, it only enabled FTP Read access. There is nowhere in the creation of the rule, in the ‘Properties’ of the rule, or in the properties of the default FTP object to specify read/write access. Nor does it inform you that the default permission is being set as read only. You have to click right click on the rule you created and choose “Configure FTP” (not ‘Properties’) to uncheck the Read Only status of the rule. I suppose that this follows the general IT best practice of enabling only minimal required privileges, but some documentation or forewarning would’ve been nice! Consider yourself forewarned!
