
- Products
- Services
- About
- Resources

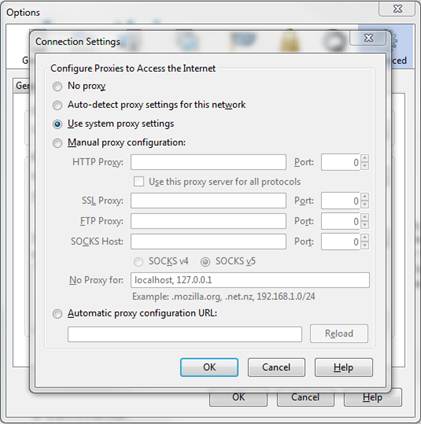
Do you ever get tired of changing your proxy settings inside Firefox to match the settings of the location you are at that day? If you answered yes, then “Use system proxy settings” is for you. When this option is selected, Firefox will set the proxy settings automatically. This has been very useful when moving from our office to a customer site to my house, where each uses different proxy settings. To set your proxy settings to “Use system proxy settings” in Firefox follow the instructions below. [more]
1) Open Firefox
2) Tools > Options > Advanced > Network > Settings > Use system proxy settings
This is sort of a follow up to a post about the Firefox addon Certificate Patrol. The addon Perspectives also helps watch out for certificate related problems. When you go to a secure web site, Perspectives can (with a click or automatically) check with several “notaries” scattered around the world and tell you whether they are getting the same certificate from that site as you are. Read http://perspectives-project.org/ for more details. Here is a link to the Firefox addon: https://addons.mozilla.org/en-US/firefox/addon/perspectives. There is also an Alpha, very experimental Chrome addon https://chrome.google.com/webstore/detail/lnppfgdnjafeikakadfopejdpglpiahn.
This project is out of Carnegie Mellon University The notary server is open source, so anyone can run their own servers. By default, the plugin uses several servers that seem to be run by the Massachusetts Institute of Technology.
This approach is certainly not for everyone, but here is what I have done to mitigate the problem with so many certificate authorities out there. The Comodo breach of March 2011, for example, allowed some bad guys to use a registration authority to generate valid certificates for Google, Yahoo, Skype, etc. There are companies that sell boxes with software that will generate a valid certificates on the fly for every secure web site you visit in order to be able to observe your traffic. With so many CAs, the risk of misuse has increased. These comments mainly apply to Windows.
I think it was during May 2010, I edited the trust level on the root CA certificates in Firefox to only trust about 10 of them. I think I have had to trust maybe two more since then. I started with the list at http://netsekure.org/2010/05/results-after-30-days-of-almost-no-trusted-cas. There are several links on this page that explain a lot about how Windows handles certificates. This is one of the major reasons I use Firefox instead of IE.
To change the trust level of certificates in Firefox, go to Options, select the Encryption tab, and then the View Certificates button. This brings up the Certificate Manger window. The Authorities tab in the Certificate Manage window is where all the CAs are listed. Select each certificate and then select the Edit Trust button at the bottom. This is where you can disable trusting each CA’s certificate. [more]
I also run the Firefox Addon Certificate Patrol which saves every certificate and warns me if a certificate has changed. The primary blogger with the Tor Project, phobos (I don’t know the real name), suggests being your own certificate authority in a manual sort of way and not trusting any external certificate authorities (https://blog.torproject.org/blog/life-without-ca). I decided not to go that far.
If you prefer another browser such as Google Chrome or Internet Explorer, the procedure will be different. Chrome and IE use the Windows certificate store, so you will have to delete the certificates that you do not want to trust. Opera has it’s own store, but operates like Windows, downloading additional root certificates behind your back. You may be able to preload these and remove the trust, but I have not taken the time to look into this. I know nothing about how Safari handles certificates.
As I mentioned at the begining of the article, this approach is not for everyone. However, for technical users with a little patience you can greatly reduce the likelihood you'll fall susceptible to a spoofed SSL certificate.
It’s a pain to make sure that every site you enter credentials or nonpublic information (such as credit card info) into is encrypted. I’d be willing to bet that even security aware people get complacent sometimes and assume that since amazon.com was encrypted the last time I used it, it’s probably still encrypted.
Now there’s an add-on for Firefox that makes it much more obvious when the site you’re looking at is or isn’t encrypted. It’s called “SSLPersonas”. Despite its name, you’ll need to look for it under add-ons/extensions, not themes/personas. It dynamically changes the entire web browser theme depending on what kind of page you’re on. By default, it uses your current theme for unencrypted websites (i.e. HTTP). It switches to a blue theme with a lock for HTTPS sites with a traditional certificate (i.e. not extended validation (EV)). It switches to a green theme with locks and a certificate for HTTPS sites with an EV certificate. And, finally, it switches to an orange them with a triangle and exclamation mark for HTTPS sites that have a broken/expired certificate. The themes it uses are customizable, so you could make the broken certificate use a McDonald’s Hamburgalar theme if you wanted.
The Level Platforms Service Center website is probably not very standards-compliant. We've know for some time that Firefox and Chrome browsers don’t render it properly, but I’ve recently seen more critical problems, such as the Site Management page showing a blank site-list in Chrome. Some of the monitoring procedures require these pages, so using IE (or Firefox add-on like IE Tab) may be the only way to see everything properly.
When changing some settings in Internet Explorer recently, I stumbled across the “Use SSL 3.0” and “Use TLS 1.2” settings under the Advanced tab of Internet Options. For a long time, I have been running without SSL 2.0, TLS 1.0, and TLS 1.1 enabled, but I wondered if SSL 3.0 is even necessary anymore (TLS superseded SSL 3.0 in 1999). So I unchecked the “Use SSL 3.0” check box. I did the same in my Firefox settings. I ran that way for at least a couple of weeks without any noticeable issues. Then last week I was onsite at a bank and tried to use the Cisco AnyConnect SSL VPN. It did not connect, so I tried it that night from the hotel. It still did not connect. The Cisco IPSEC VPN client worked perfectly. After a couple of days of the AnyConnect client not working, I was about to send an email to one of our network engineers asking if anything had changed when I remembered the “Use SSL 3.0” setting. After re-enabling SSL 3.0 in both IE and Firefox, the AnyConnect client worked. Aside from the SSL 3.0 setting breaking AnyConnect, the more general GOTCHA is that the AnyConnect client uses at least some of the web browser settings when establishing its connection, so I now know to include them when troubleshooting the VPN.
After recently upgrading Firefox I noticed several old versions of the Java Console under the Add-ons section. I could see the versions but could not uninstall them because the button was disabled. Uninstalling Java removed the most current version but not the old versions. After some digging I found that Firefox 3.6 started showing disabled add-ons. I was able to remove the old add-ons by going to c:\program files\Mozilla Firefox\extensions and removing the folders starting with “{CCAFE”. [more]
While looking into this I found an free tool for automating the procedure to remove old versions of Java - http://raproducts.org/javara.html
If you are using the Firefox browser, you need to make sure you are aware of the security extensions available to Firefox to help protect you while surfing the Internet. These extensions; including BetterPrivacy, BlockSite, Dr. Web Anti-virus, FormFox, Ghostery, Locationbar, NoScript, Password Hasher, QuickJava, and Web of Trust are effective in helping protect from worms, hackers, phisher, etc. While these extensions (and other security software and tools) can be valuable and effective, there is still no better security feature than good, solid, common sense.
To learn more about the security extensions available to the Firefox browser, visit http://news.cnet.com/8301-17939_109-10249214-2.html?tag=newsLatestHeadlinesArea.0